Windows Tips and Tricks
- Published: 07 February 2018 07 February 2018
Updated!
Works with Windows 7, 10 and most servers:
- GodMode: Create a folder on your desktop and rename code list below You can call it GodMode or Master Folder... What this gives you is access to all the system programs to change and work on things in windows.
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
- Snipping Tool: Takes screenshots of anything on you desktop. Then you can save it as a JPG or PNG
- Turn the Web Browser into a Note Pad, past the code below in the address bar of your browser, then just start typing
data:text/html, <textarea style="font-size: 1.5em; width: 100%; height: 100%; border: none; outline: none" autofocus /> Start Here
- Snip and Sketch: to start Windosw Key + Shift + S This will be replacing the Snipping tool in later versions of Windows 10. This tool allows you to open menus and take a screen shot unlike the snipping tool.
- Voice dictation: pressed windows key and H start dictation you need to be an A text field such as a work processor or a field browser.
- Virtual Desktops - Win 10 now has mutable desktop views ( just like Linux). press Windows key and TAB then click new desktop. switch between the with Windows key and Ctrl and right or left arrow.
- Magnifier - Use the Windows Key and the + and - keys to magnify the entire desktop.
- Quick Assist - to Get Assistance or to Give Assistance - A new feature within win 10 that allows you to share desktops. It give you the asister an access code and password to allow you access to someone desktop. As a hosts you will need an MS account to complete the connection. It's similar to Teamviewer but through MS
- Sticky Notes: Handy desktop tool to jot down a quick not. In windows 10 you have other options to enable "Insights". this adds more functions...
- Windows Remote Assistance: it works great on the Intranet such as home to connect two windows machines. you can also use the remote assistance to connect to another persons computer over the internet. Use the wizard to connect. If you do not use this feature you should disable it in your settings menu.
- Steps Recorder: can record all you steps while you click and type on your system. This could be good for troubleshooting problems or making instructional screenshots on home to do something.
- Voice Recorder or Sound recorder: either one may be on your system based on the windows version you are using.
- MRT: Malicious Removal Tool: you should run this from time-to-time. This will not run automatically unless windows updater is running, so you need to run in manually via the run menu.
- SyncTool: this is a FREE Microsoft product and is very useful to sync your files with USB hard drive, DropBox, OneDrive, Search for ms synctool and only download it from Microsoft. This is the current link -> https://www.microsoft.com/en-us/download/details.aspx?id=15155 Go thought the setup wizard to manage your files. Now you can you Windows Task Scheduler and have it run every hours while your logged into your system. use command below:
[code]cd \Program Files\SyncToy 2.1\
SyncToycmd.exe -R[/code]
- certUtil: is a Checksum tool, Yes you will need to run this at the CMD window but is worth mentioning here. I wrote a blog on it here...
- Windows time and alarms: You can set alarms and timers. In addition you can see a world clock and see the difference between several locations.
- Windows 10 Game Mode: To start press Windows key and G. This will bring up MS game mode which add several features such at game recorder, chat, audio widget.
- Ransomware protection: go to Windows Security to virus and protection and scroll down and click ransomware protection. This locks very important files that cannot be accessed by remote software. If you are using other antivirus protections this feature will no show.
- Reliability Monitory: Windows 10 now has a tool that gives widows historical reliability issues. This tool shows errors, warning, and info historically and gives possibly resolutions.
FCC Approves FM Mode for CB Radios: The Biggest Change in Four Decades
- Published: 18 February 2023 18 February 2023
The Federal Communications Commission (FCC) has recently approved the use of FM mode on Citizen Band Radios (CB radios), which is the biggest change in CB radio technology in the United States since the late 1970s. CB radios have traditionally used AM and single-sideband (SSB) modes, but the addition of FM mode offers several advantages, particularly in terms of voice quality and reduced background noise.
According to the Department of Electrical Engineering and Computer Sciences at U.C. Berkeley, FM mode provides an "improved signal to noise ratio (about 25dB) with regards to man-made interference" compared to AM, which could significantly reduce background noise interference and improve voice quality. This development could be particularly beneficial for truckers, who are among the top users of CB radios in the United States.
Professional users of the CB radio band, such as truckers, have long faced challenges communicating effectively, especially during peak times when solar cycles can interfere with signals. However, the addition of FM mode is expected to cut down on this interference and offer a more reliable communication method for professional users.
In summary, the FCC's approval of FM mode for CB radios represents a significant advancement in the technology, offering improved voice quality and reduced background noise interference. This development is expected to be particularly beneficial for professional users of CB radios, such as truckers.
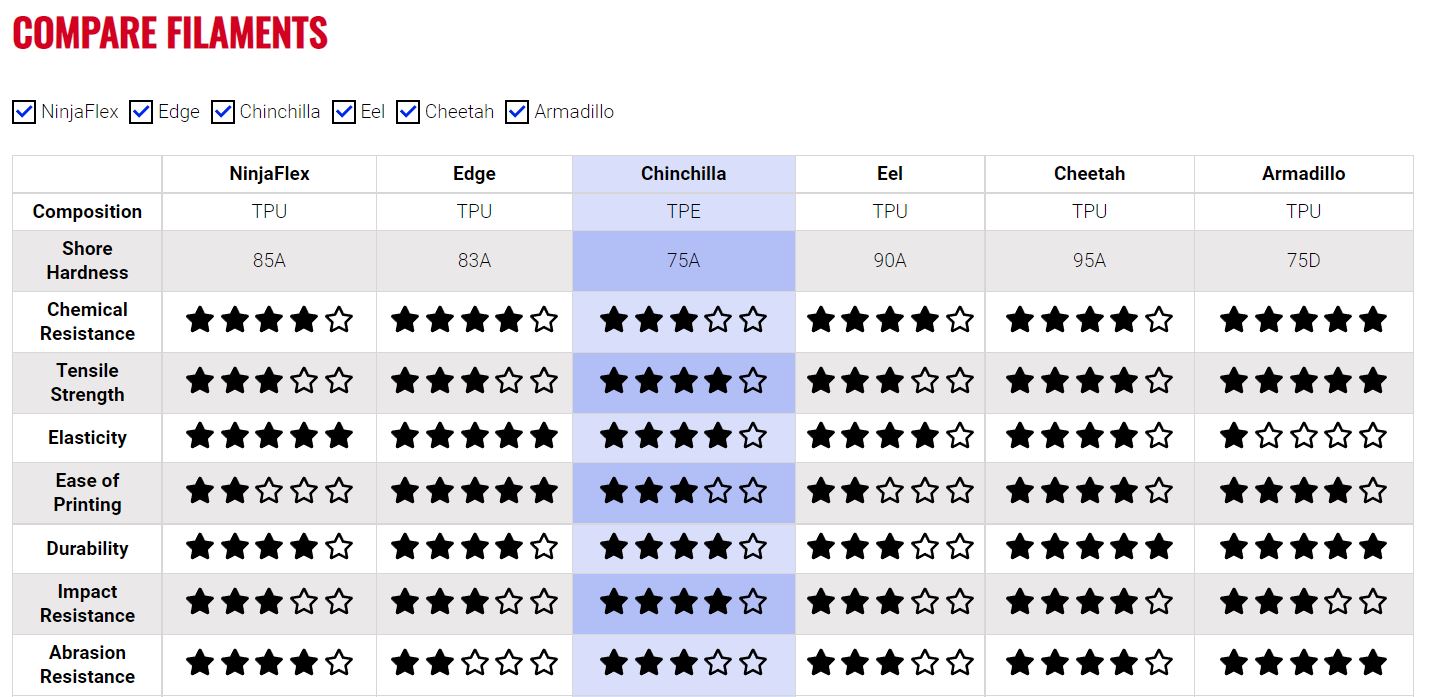
TPU 3D Filament, Shore Hardness Comparison
- Published: 12 September 2022 12 September 2022
Note: For all industrial 3D printing see Stratasys.com Material List
Shore Hardness
Shore hardness is a common term you’ll hear when it comes to polymers for fileable 3D printer Filament, but it’s more general than the more technical measurements like Young’s modulus or elongation at break. For example, most flexible filament would be Shore A, and within the A category they would have individual values, such as Shore hardness 95A. You may also see Shore values in the C or D category, which more often denote hard rubbers and semi-rigid plastics. The most common Shore value for flexible filaments is 95A. Using the chart below will help you determine what TPU 3D printer filament to buy.
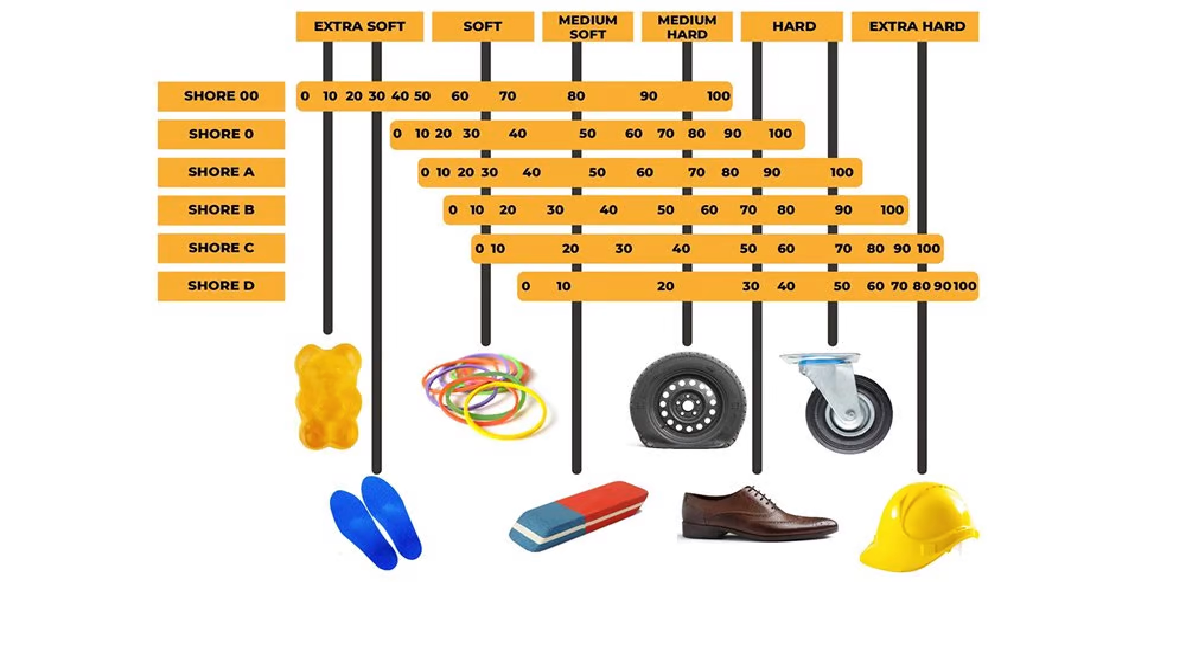
Some examples from NINJATEK:
- Use NinjaFlex® (85A) for grip pads, vibration dampening, shock absorption, gaskets, seals, guards and soft robotics. For RC tires, seals and gaskets.
- Use Cheetah® (95A) for assembly line jigs, fixtures, ergonomic improvements, guards and shock absorption.
- Use Armadillo® (75D) for jigs, fixtures, ergonomic improvements, proof-of-concept gears, sprockets, shipping inserts, textured rollers and small part replacements. For medical for prosthetic sockets and shells.
- Use Eel™ (90A) for robotic grippers. TPU 3D printing filament is a conductive, static dissipative and flexible material.
- Use Chinchilla™ (75A) for prosthetic liners and organ printing (pre-surgery prep or teaching hospitals). for clothing, cosplay costumes and wearables such as watch bands. for non-marking applications.
Site Info: link
Mechanize Setup
- Published: 08 September 2022 08 September 2022
The following is the standard setup for mechanize. the most current browser and window's OS/code]
[code]
import mechanize
# setting up the Mechanize browser headers
br = mechanize.Browser()
user_agent = [('user-agent', 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36 Edg/105.0.1343.27')]
#br.set_all_readonly(False) # allow everything to be written to
br.set_handle_robots(False) # ignore robots
br.set_handle_refresh(False) # can sometimes hang without this
br.addheaders = user_agent
url = 'https://johnkosh.com'
[/code]
47 Confucian Proverbs
- Published: 31 August 2022 31 August 2022
Confucian proverbs have the power to transform lives, but they are not for casual reading. When you read them once, you feel the power of his words; read twice, and you will appreciate his deep thought; read them over and over again, and you will be enlightened. Let these Confucian quotes guide you in life.
- "Everything has beauty, but not everyone sees it."
- "They must often change who would be constant in happiness or wisdom."
- "What the superior man seeks is in himself; what the small man seeks is in others."
- "In a country well governed, poverty is something to be ashamed of. In a country badly governed, wealth is something to be ashamed of."
- "It does not matter how slowly you go so long as you do not stop."
- "When anger rises, think of the consequences."
- "When it is obvious that the goals cannot be reached, don't adjust the goals; adjust the action steps."
- "Faced with what is right, to leave it undone shows a lack of courage."
- "To be able under all circumstances to practice five things constitutes perfect virtue; these five things are gravity, generosity of soul, sincerity, earnestness, and kindness."
- "To see what is right, and not to do it, is want of courage or of principle."
- "Fine words and an insinuating appearance are seldom associated with true virtue."
- "Before you embark on a journey of revenge, dig two graves."
- "Success depends upon previous preparation, and without such preparation, there is sure to be failure."
- "Do not impose on others what you yourself do not desire."
- "Men's natures are alike, it is their habits that carry them far apart."
- "Our greatest glory is not in never falling, but in rising every time we fall."
- "Real knowledge is to know the extent of one's ignorance."
- "Hold faithfulness and sincerity as first principles."
- "I hear and I forget. I see and I remember. I do and I understand."
- "Respect yourself and others will respect you."
- "Silence is a true friend who never betrays."
- "The superior man, when resting in safety, does not forget that danger may come. When in a state of security he does not forget the possibility of ruin. When all is orderly, he does not forget that disorder may come. Thus his person is not endangered, and his States and all their clans are preserved."
- "The will to win, the desire to succeed, the urge to reach your full potential... these are the keys that will unlock the door to personal excellence."
- "Better a diamond with a flaw than a pebble without."
- "Study the past if you would define the future."
- "Wheresoever you go, go with all your heart."
- "Wisdom, compassion, and courage are the three universally recognized moral qualities of men."
- "Forget injuries, never forget kindnesses."
- "Have no friends not equal to yourself."
- "He who exercises government by means of his virtue may be compared to the north polar star, which keeps its place and all the stars turn towards it."
- "He who learns but does not think is lost! He who thinks but does not learn is in great danger."
- "He who speaks without modesty will find it difficult to make his words good."
- "Life is really simple, but we insist on making it complicated."
- "A superior man is modest in his speech but exceeds in his actions."
- "Be not ashamed of mistakes and thus make them crimes."
- "The more man meditates upon good thoughts, the better will be his world and the world at large."
- "The superior man understands what is right; the inferior man understands what will sell."
- "By nature, men are nearly alike; by practice, they get to be wide apart."
- "He who will not economize will have to agonize."
- "When we see men of a contrary character, we should turn inwards and examine ourselves."
- "He with whom neither slander that gradually soaks into the mind, nor statements that startle like a wound in the flesh, are successful may be called intelligent indeed."
- "If I am walking with two other men, each of them will serve as my teacher. I will pick out the good points of the one and imitate them, and the bad points of the other and correct them in myself."
- "Choose a job you love, and you will never have to work a day in your life."
- "If you look into your own heart, and you find nothing wrong there, what is there to worry about? What is there to fear?"
- "Ignorance is the night of the mind, but a night without moon and star."
- "It is easy to hate and it is difficult to love. This is how the whole scheme of things works. All good things are difficult to achieve, and bad things are very easy to get."
- "Without feelings of respect, what is there to distinguish men from beasts?"
From: 47 Confucius Quotes That Still Ring True Today (thoughtco.com)
MS Teams New Tips 2021
- Published: 12 April 2021 12 April 2021
Topics Covered
- 00:27 Noise suppression
- 2:31 Transfer meeting devices
- 03:35 Teams for personal use
- 04:40 Switch accounts
- 05:07 Polls during meetings
- 06:28 Pin posts
- 07:29 Additional status controls
- 08:28 Improved notifications
- 09:06 Mute attendees
- 10:52 Insight
- 12:29 Templates
- 13:27 Emojis in Teams & Channels
Thanks to Kevin Stratvert his Channel ->https://www.youtube.com/channel/UCfJT_eYDTmDE-ovKaxVE1ig
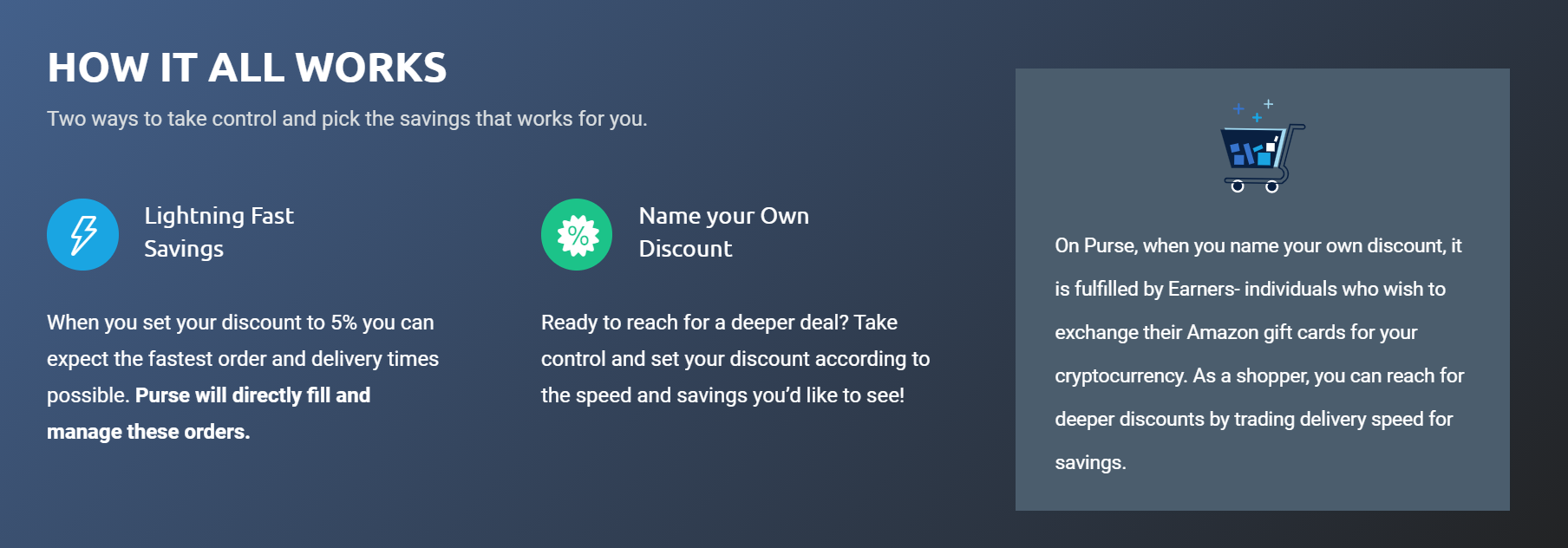
Use Bitcoin to Buy on Amazon
- Published: 30 November 2020 30 November 2020
I have waited a long time to spend my (Tiny Bit) of Bitcoin BTC, but now I have found a place to easily spend this cryptocurrency. What is even better it is directly linked to Amazon. So what ever you want from Amazon Purse.io will allow you to use your Bitcoin and Bitcoin Cash to get what you want. The easiest way to do this is search your product on amazon and copy the ASIN number into your Purse.io account.
So to get started click this link Purse.io add some BTC or BCH to your account and start shopping. Yes, Purse.io has a complete shopping area directly linked to Amazon so you can start shopping there.
And as an ADDED BONUS you can name your discount... Yes, never pay full price for an Amazon product again. I have bought several items with Purse.io and have received as much as 15% off my items.
Windows 10 File Explorer Search
- Published: 15 October 2020 15 October 2020
Need to find a part number within a PDF, DOC, TEX file? Windows File Explorer has a search feature that will look into your document and find what you need.
Example below I am searching for Freight with in a PDF within a Date of this year.
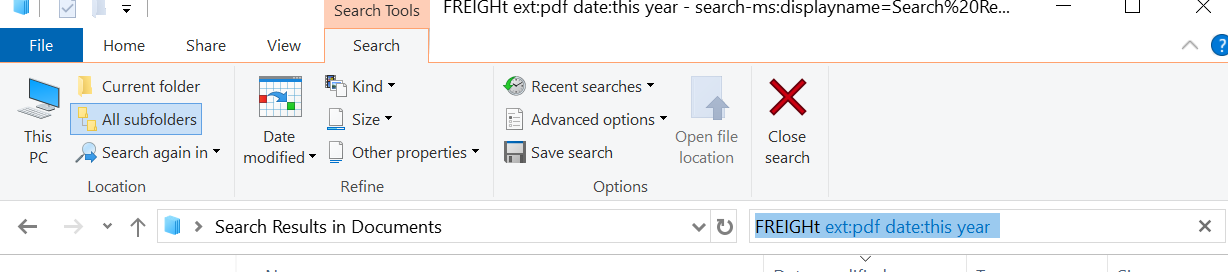
More search syntax is available at MS website:
https://docs.microsoft.com/en-us/windows/win32/lwef/-search-2x-wds-aqsreference
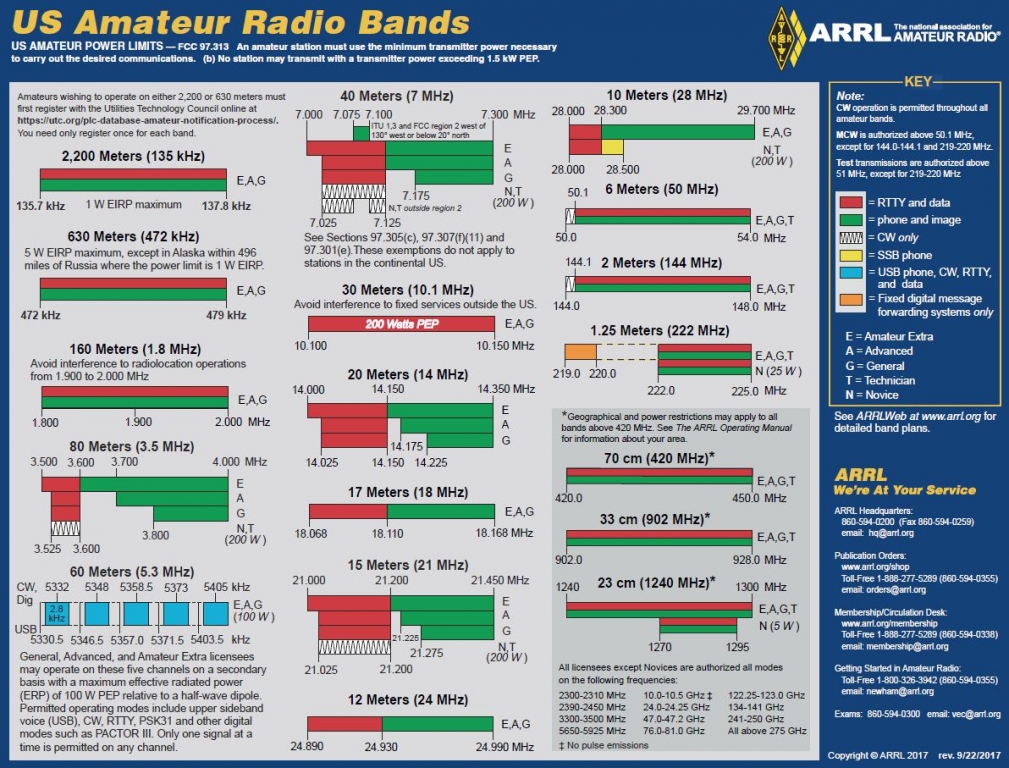
Ham Info
- Published: 23 January 2012 23 January 2012
Coordinates Lat: 40.21022 Lon: -75.09248 Grid: FN20kf
This infor was found on http://www.qrz.com/gridfinder
GMRS
Check out the Puxing 777 I purchased for GRMS. The units are open and programmable for most UHF frequencies See here
| me | Lower frequency (repeater output) (MHz) | Upper frequency (repeater input) (MHz) | Motorola convention | Icom F21-GM convention | Notes |
| "550" | 462.55 | 467.55 | Ch. 15 | Ch. 1 | |
| "575" | 462.575 | 467.575 | Ch. 16 | Ch. 2 | |
| "600" | 462.6 | 467.6 | Ch. 17 | Ch. 3 | |
| "625" | 462.625 | 467.625 | Ch. 18 | Ch. 4 | |
| "650" | 462.65 | 467.65 | Ch. 19 | Ch. 5 | Use not permitted near the Canadian border. |
| "675" | 462.675 | 467.675 | Ch. 20 | Ch. 6 | Often used as emergency and road information calling frequency with tone squelch of 141.3 Hz. |
| "700" | 462.7 | 467.7 | Ch. 21 | Ch. 7 | Use not permitted near the Canadian border. |
| "725" | 462.725 | 467.725 | Ch. 22 | Ch. 8 |
Refference from https://radiofreeq.wordpress.com
| Location | Name | Frequency | Duplex | Offset | Tone | rToneFreq | cToneFreq | DtcsCode | DtcsPolarity | Mode | TStep |
| 0 | FRS 01 | 462.5625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 1 | FRS 1 | 462.5625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 2 | FRS 2 | 462.5875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 3 | FRS 3 | 462.6125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 4 | FRS 4 | 462.6375 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 5 | FRS 5 | 462.6625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 6 | FRS 6 | 462.6875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 7 | FRS 7 | 462.7125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 8 | FRS 8 | 467.5625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 9 | FRS 9 | 467.5875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 10 | FRS 10 | 467.6125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 11 | FRS 11 | 467.6375 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 12 | FRS 12 | 467.6625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 13 | FRS 13 | 467.6875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 14 | FRS 14 | 467.7125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 12.5 | |
| 15 | GMRS15 | 462.55 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 16 | GMRS16 | 462.575 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 17 | GMRS17 | 462.6 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 18 | GMRS18 | 462.625 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 19 | GMRS19 | 462.65 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 20 | GMRS20 | 462.675 | 0 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 | |
| 21 | GMRS21 | 462.7 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 22 | GMRS22 | 462.725 | 0 | Tone | 67 | 67 | 23 | NN | FM | 25 | |
| 23 | GMR15R | 462.55 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 24 | GMR16R | 462.575 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 25 | GMR17R | 462.6 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 26 | GMR18R | 462.625 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 27 | GMR19R | 462.65 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 28 | GMR20R | 462.675 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 29 | GMR21R | 462.7 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 30 | GMR22R | 462.725 | + | 5 | Tone | 141.3 | 141.3 | 23 | NN | FM | 25 |
| 31 | PMR 1 | 446.00625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 32 | PMR 2 | 446.01875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 33 | PMR 3 | 446.03125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 34 | PMR 4 | 446.04375 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 35 | PMR 5 | 446.05625 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 36 | PMR 6 | 446.06875 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 37 | PMR 7 | 446.08125 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 38 | PMR 8 | 446.09375 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 6.25 | |
| 39 | MURS 1 | 151.82 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 5 | |
| 40 | MURS 2 | 151.88 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 5 | |
| 41 | MURS 3 | 151.94 | 0 | Tone | 67 | 67 | 23 | NN | NFM | 5 | |
| 42 | MURS 4 | 154.57 | 0 | Tone | 67 | 67 | 23 | NN | FM | 5 | |
| 43 | MURS 5 | 154.6 | 0 | Tone | 67 | 67 | 23 | NN | FM | 5 | |
| 44 | BUSRED | 151.625 | 0 | Tone | 67 | 67 | 23 | NN | FM | 5 | |
| 45 | BUSPUR | 151.955 | 0 | Tone | 67 | 67 | 23 | NN | FM | 5 | |
| 46 | MAR01A | 156.05 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 47 | MAR03A | 156.15 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 48 | MAR05A | 156.25 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 49 | MAR06 | 156.3 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 50 | MAR07A | 156.35 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 51 | MAR08 | 156.4 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 52 | MAR09 | 156.45 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 53 | MAR10 | 156.5 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 54 | MAR11 | 156.55 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 55 | MAR12 | 156.6 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 56 | MAR13 | 156.65 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 57 | MAR14 | 156.7 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 58 | MAR15 | 156.75 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 59 | MAR16 | 156.8 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 60 | MAR17 | 156.85 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 61 | MAR18A | 156.9 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 62 | MAR19A | 156.95 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 63 | MAR20A | 157 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 64 | MAR21A | 157.05 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 65 | MAR22A | 157.1 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 66 | MAR23A | 157.15 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 67 | MAR62 | 156.125 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 68 | MAR63A | 156.175 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 69 | MAR65A | 156.275 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 70 | MAR66A | 156.325 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 71 | MAR67 | 156.375 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 72 | MAR68 | 156.425 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 73 | MAR69 | 156.475 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 74 | MAR71 | 156.575 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 75 | MAR72 | 156.625 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 76 | MAR73 | 156.675 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 77 | MAR74 | 156.725 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 78 | MAR75 | 156.775 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 79 | MAR76 | 156.825 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 80 | MAR77 | 156.875 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 81 | MAR78A | 156.925 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 82 | MAR79A | 156.975 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 83 | MAR80A | 157.025 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 84 | MAR81A | 157.075 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 85 | MAR88A | 157.425 | 0 | 67 | 67 | 23 | NN | FM | 5 | ||
| 86 | WX 1 | 162.55 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 87 | WX 2 | 162.4 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 88 | WX 3 | 162.475 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 89 | WX 4 | 162.425 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 90 | WX 5 | 162.45 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 91 | WX 6 | 162.5 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 92 | WX 7 | 162.525 | off | 0 | 67 | 67 | 23 | NN | FM | 5 | |
| 93 | SAREMT | 155.16 | 0 | Tone | 127.3 | 127.3 | 23 | NN | FM | 5 | |
| 94 | HAM 42 | 146.42 | 0 | Tone | 100 | 100 | 23 | NN | FM | 5 | |
| 95 | HAM 52 | 146.52 | 0 | Tone | 100 | 100 | 23 | NN | FM | 5 | |
| 96 | HAM 55 | 146.55 | 0 | Tone | 100 | 100 | 23 | NN | FM | 5 | |
| 97 | HAMUHF | 446 | 0 | Tone | 100 | 100 | 23 | NN | FM | 5 | |
| 98 | HAM U3 | 446.03 | 0 | Tone | 100 | 100 | 23 | NN | FM | 5 |
Shortwave
PRIME TIME SHORTWAVE - http://www.primetimeshortwave.com English shortwave broadcasts sorted by time Relay site codes: ae-United Arab Emirates, al-Albania, ar-Armenia, as-Ascension, au-Austria, bt-Botswana, bu-Bulgaria, ch-China, cu-Cuba, cy-Cyprus, fr-France, ge-Germany, gr-Greenville USA, ka-Kazakhstan, ko-South Korea, ku-Kuwait, ma-Madagascar, ml-Mali, mo-Moldova, nm-North Mariana Islands, om-Oman, pa-Palau, ph-Philippines, ro-Romania, ru-Russia, rw-Rwanda, sa-Sao Tome e Principe, se-Seychelles, si-Singapore, sl-Sri Lanka, sp-Spain, ta-Taiwan,th-Thailand, tj-Tajikistan, uk-United Kingdom, uz-Uzbekistan, va-Santa Maria Vatican, wb-WWRB USA, wc-WWCR USA, wh-WHRI USA, wi-WINB USA, wq-WBCQ USA, wr-WRMI USA, wt-WTWW USA. za-South Africa Notes -- Days of week: Su-Sunday, M-Monday, Tu-Tuesday, W-Wednesday, Th-Thursday, F-Friday, Sa-Saturday, exW-except Wednesday Target areas: Af-Africa, Am-America, As-Asia, Eu-Europe, LA-Latin America, ME-Middle East, NA-North America, Oc-Oceania/Australia; Other: alt-alternate frequency, drm-Digital Radio Mondiale, occ-occasional use, le-Learning English G24-Global 24 Radio This page was last updated by Ernest Riley on July 24, 2015. Version A15v05 UTC Time Notes Country Station Frequencies 0000-0030 NA Egypt R. Cairo 9965 0000-0045 As India All India R. 9690, 9705, 11645 drm, 11710, 13605 drm 0000-0100 As United Kingdom BBC 6005om, 9755th, 12095si 0000-0100 Eu China China R. Int'l 7350 0000-0100 As China China R. Int'l 6075, 6180, 7425, 11790, 11885, 13750, 15125 0000-0100 LA, Tu-Sa U. S. A. KVOH 9975 0000-0100 Am,Tu-F U. S. A. Overcomer Ministry5110wq 0000-0100 Eu, M U. S. A. Overcomer Ministry5920wh 0000-0100 Am, M U. S. A. Overcomer Ministry7490wq 0000-0100 Oc Australia R. Australia 15240, 15415, 17840 0000-0100 NA Romania R. Romania Int'l 9730, 11800 0000-0100 NA Thailand R. Thailand 15590 0000-0100 Am, Sa U. S. A. WBCQ 5110 0000-0100 NA, Tu-Sa U. S. A. WHRI 5920 0000-0100 NA U. S. A. WHRI 7385 0000-0100 LA U. S. A. WHRI 7315 0000-0100 NA U. S. A. Wld Univ Network 13845 0000-0100 NA U. S. A. WWCR1 6115 0000-0200 NA China China R. Int'l 6020al, 9570al 0000-0200 LA U. S. A. Overcomer Ministry7730wr 0000-0200 Oc, M-Sa New Zealand RNZI 17675 drm 0000-0200 NA,Eu U. S. A. WTWW 9475 0000-0200 NA, Tu-Sa U. S. A. WWCR4 7520 0000-0200 NA U. S. A. WWRB 3215, 5050 0000-0300 NA, Su Netherlands Mighty KBC Radio 9925ge 0000-0300 Af U. S. A. Overcomer Ministry15190wr 0000-0300 Eu U. S. A. WRMI 11580 0000-0400 Am, Su-M U. S. A. WBCQ 5110 0000-0430 LA U. S. A. WINB 9265 0000-0458 Oc New Zealand RNZI 15720 0000-0500 Am U. S. A. WBCQ 9330 0000-0500 LA U. S. A. WRMI 9955 0000-0700 Oc Vanuatu R. Vanuatu 7260 0000-0900 Af U. S. A. WEWN 11520 0000-1000 NA U. S. A. Overcomer Ministry7570wr 0000-1000 Am Anguilla Wld Univ Network 6090 0000-1200 NA U. S. A. WWCR3 4840 0000-1400 NA U. S. A. Overcomer Ministry3185wb 0000-2100 Eu U. S. A. Overcomer Ministry15770wr 0000-2400 As Diego Garcia AFRTS 12759 USB 0000-2400 NA Canada CFRX 6070 0000-2400 NA Canada CFVP 6030 0000-2400 NA Canada CKZU 6160 0000-2400 Domestic Malaysia RTM Malaysia 7295 0000-2400 NA U. S. A. TruNews 9395wr 0015-0030 LA, M Cyprus FG Radio 9955wr 0030-0100 LA, Tu-Sa Czech Republic R. Prague 9955wr 0030-0100 NA Slovakia R. Slovakia 5850wr, 11580wr 0030-0100 Eu Ukraine R. Ukraine Int'l 11580wr 0030-0100 Eu Ukraine R. Ukraine Int'l 11580wr 0100-0128 NA Vietnam V. of Vietnam 12005uk 0100-0200 As United Kingdom BBC 12095si, 15660th 0100-0200 NA China China R. Int'l 9580cu 0100-0200 As China China R. Int'l 6180, 9470, 9535, 11870, 15125, 15785 0100-0200 Eu China China R. Int'l 9675 0100-0200 Oc Australia R. Australia 15240, 15415, 17840 0100-0200 As,ME,Eu Tajikistan V. of Tajik 7245 0100-0200 NA U. S. A. WHRI 7385 0100-0200 LA, Su-M U. S. A. WHRI 7315 0100-0200 NA, Tu-Sa U. S. A. WHRI 5920 0100-0200 NA U. S. A. WTWW 12105 0100-0300 Am U. S. A. Overcomer Ministry7490wq 0100-0300 As, Su Palau T8WH 17725 0100-0300 As, Su Palau T8WH 17750 0100-0400 LA U. S. A. KVOH 9975 0100-0400 LA U. S. A. Overcomer Ministry5050wb 0100-0400 Am, Tu-Sa U. S. A. Overcomer Ministry5110wq 0100-0500 NA Cuba R. Havana Cuba 6000, 6165 0100-0700 NA U. S. A. TruNews 5850wr, 7455wr 0100-0900 NA U. S. A. WWCR1 3215 0100-1200 Af U. S. A. Wld Univ Network 5935wc 0100-2300 Eu U. S. A. Overcomer Ministry11580wr 0130-0200 NA, Tu-Su Albania R. Tirana 9850 0130-0200 As Myanmar Thazin R. 6030 0140-0159 As Vatican City Vatican R. 11730, 15470ph 0145-0200 LA, Th Cyprus FG Radio 9955wr 0200-0215 As, Tu Canada Bible Voice 11945ma 0200-0215 NA, M U. S. A. Eternal Good News 7385wh 0200-0230 As, Th,Sa Canada Bible Voice 11945ma 0200-0230 NA Thailand R. Thailand 15590 0200-0300 As United Kingdom BBC 12095om, 15660th 0200-0300 As, Su Canada Bible Voice 11945ma 0200-0300 As China China R. Int'l 11770, 13640 0200-0300 LA South Korea KBS World R. 9580 0200-0300 As South Korea KBS World R. 9690 0200-0300 Eu U. S. A. Overcomer Ministry5920wh 0200-0300 Oc Australia R. Australia 15240, 15415, 17840 0200-0300 LA U. S. A. WHRI 7315 0200-0300 NA, Tu-Sa U. S. A. WWCR4 5890 0200-0330 NA Egypt R. Cairo 9720, 9315 alt, 9835 alt, 9860 alt 0200-0330 ME Philippines R. Pilipinas 15640, 17700, 17820 0200-0400 Am, M U. S. A. WBCQ 7490 0200-0500 Am U. S. A. WRNO 7506.4 0200-0500 NA U. S. A. WWRB 3195, 5050 0200-1400 NA,Eu,Af U. S. A. WTWW 5830 0215-0300 NA U. S. A. WHRI 7385 0230-0300 NA Vietnam V. of Vietnam 12005uk 0255-0400 Oc New Zealand RNZI 17675 drm 0300-0327 Af Vatican City Vatican R. 7360, 9660 0300-0327 As Vatican City Vatican R. 15470uz 0300-0330 LA, Su-M Czech Republic R. Prague 9955wr 0300-0330 Af, Su Swaziland TWR Africa 3200 0300-0330 Eu, Su U. S. A. WHRI 7520 0300-0330 LA,Tu,F-Su U. S. A. WINB 9265 0300-0355 NA, Eu Turkey V. of Turkey 9515 0300-0355 ME Turkey V. of Turkey 6165 0300-0400 ME United Kingdom BBC 9440om, 12095om 0300-0400 Af, M-F South Africa Channel Africa 3345, 5980 0300-0400 NA China China R. Int'l 9790cu 0300-0400 As China China R. Int'l 11770, 13590, 13620, 15110, 15120, 15785 0300-0400 NA, Tu-Sa U. S. A. Overcomer Ministry5890wc 0300-0400 LA U. S. A. Overcomer Ministry5985wr 0300-0400 Am U. S. A. Overcomer Ministry7490wq 0300-0400 Oc Australia R. Australia 15240, 15415, 17840 0300-0400 NA Romania R. Romania Int'l 9730, 11800 0300-0400 As Romania R. Romania Int'l 11825, 15220 drm 0300-0400 Af Oman R. Sultanate Oman 15355 0300-0400 As Taiwan R. Taiwan Int'l 15320 0300-0400 NA,Tu-Sa Argentina RAE 11711 0300-0400 As Palau T8WH 17725 0300-0400 As, Su-F Palau T8WH 17750 0300-0400 Af U. S. A. V. of America 4930bt, 6080bt, 9885bt, 15580bt 0300-0400 Am, Tu-Sa U. S. A. WBCQ 7490 0300-0400 NA, Tu-Sa U. S. A. WHRI 5920 0300-0400 NA U. S. A. WHRI 7385 0300-0400 NA, Su-M U. S. A. WWCR4 5890 0300-0600 Af Sudan Miraya FM R 9940mo 0300-2100 ME Bahrain R. Bahrain 6010 USB 0320-0420 NA Iran VOIRI (VO Justice)11780, 13650 0330-0400 Af Swaziland TWR Africa 3200 0330-0400 LA Vietnam V. of Vietnam 6175wh 0330-0430 LA, Tu,Sa U. S. A. WINB 9265 0400-0430 Af U. S. A. V. of America 9885bt 0400-0430 NA U. S. A. WHRI 7385 0400-0457 Af Germany Deutsche Welle 9800ma 0400-0457 LA North Korea V. of Korea 11735, 13760, 15180 0400-0457 As North Korea V. of Korea 7220, 9445, 9730 0400-0500 Af United Kingdom BBC 7360za, 15420ae 0400-0500 ME United Kingdom BBC 12095om, 13660om 0400-0500 Af, M-F South Africa Channel Africa 3345 0400-0500 As China China R. Int'l 13590, 15120, 15785, 17730, 17855 0400-0500 Af Germany Deutsche Welle 15275ae 0400-0500 Oc Australia R. Australia 15240, 15415, 17840 0400-0500 Af, M-F Swaziland TWR Africa 3200, 4775 0400-0500 Af U. S. A. V. of America 4930bt, 4960sa, 6080sa, 15580bt 0400-1100 NA U. S. A. Overcomer Ministry5890wc 0415-0430 LA, W,F Cyprus FG Radio 9955wr 0445-0500 Eu,Sa U. S. A. Eternal Good News 11635wh 0445-0500 Eu, Sa U. S. A. WHRI 11635 0459-0758 Oc New Zealand RNZI 11725 0500-0527 Af Vatican City Vatican R. 9660ma, 11625 0500-0530 LA, Sa France R. France Int'l 9955wr 0500-0530 Eu Japan R. Japan 5975uk 0500-0530 Af Japan R. Japan 11970fr 0500-0557 As North Korea V. of Korea 13650, 15105 0500-0600 Af United Kingdom BBC 3255za, 5875as, 6005as, 6190za, 7445as, 11945za, 15420ae 0500-0600 Eu United Kingdom BBC 3955 drm 0500-0600 As China China R. Int'l 11895, 15350, 15465, 17540, 17730, 17855 0500-0600 ME China China R. Int'l 11710al 0500-0600 Af, ME China China R. Int'l 17510 0500-0600 Af Germany Deutsche Welle 7425za, 15275ma 0500-0600 Oc Australia R. Australia 15240, 15415, 17840 0500-0600 LA Cuba R. Havana Cuba 5040 0500-0600 Af U. S. A. V. of America 4930bt, 6080sa, 15580bt 0500-0700 Af, M-F South Africa Channel Africa 6145 0500-0700 Am Cuba R. Havana Cuba 6000, 6060, 6100, 6165 0500-0700 Af Nigeria V. of Nigeria 15120 0500-0800 Af Swaziland TWR Africa 4775 Sa-Su, 6120, 9500 0505-0530 Af, M-F U. S. A. V. of America 7350bt, 9815bt, 11905sa 0515-0600 Eu, F U. S. A. WHRI 11635 0530-0600 Eu Romania R. Romania Int'l 9700, 11800 drm 0530-0600 Oc, As Romania R. Romania Int'l 17760, 21500 0530-0600 Eu Thailand R. Thailand 17640 0600-0605 Oc, Sa-Su Australia R. Australia 15240, 15415, 17840 0600-0630 As Laos Lao National Radio7145 0600-0657 As North Korea V. of Korea 7220, 9445, 9730 0600-0700 Af United Kingdom BBC 6005as, 6190za, 9410za, 12095za, 13580ma, 15105, 15420ae 0600-0700 Af, M-F South Africa Channel Africa 15255 0600-0700 As China China R. Int'l 11895, 13645, 15350, 15465, 17640, 17710 0600-0700 ME China China R. Int'l 11750al, 11870, 15145 0600-0700 Af, ME China China R. Int'l 17510 0600-0700 Af U. S. A. V. of America 6080sa, 15580bt 0600-1100 LA U. S. A. Overcomer Ministry9955wr 0605-0630 Oc Australia R. Australia 15240, 15415, 17840 0630-0645 ME, M-Sa Vatican City Vatican R. 15595 0630-0700 As Myanmar Thazin R. 9460 0630-0700 Af Vatican City Vatican R. 11625, 13765 0651-0758 Oc, M-F New Zealand RNZI 7330 drm 0700-0730 Eu, Sa Canada Bible Voice 5945ge 0700-0730 Eu, Su Canada Bible Voice 5945ge 0700-0730 As Myanmar Myanmar R. 9731 0700-0800 Af United Kingdom BBC 6190za, 9410za, 11770as, 12095as, 13580ma, 13660as, 15420ae, 17830za 0700-0800 As China China R. Int'l 11895, 13660, 15350, 15465, 17540, 17710 0700-0800 Af Germany Deutsche Welle 15275fr, 15560as 0700-0800 As China PBS Zizang Lhaza 4905, 4920, 6025, 6110, 6130, 6200, 9490, 9580 0700-0800 Oc Australia R. Australia 15240, 15415, 17840 0700-0900 Af, ME China China R. Int'l 17670 0700-0900 Eu China China R. Int'l 13710al, 17490 0700-0900 LA U. S. A. Overcomer Ministry7315wh 0700-1000 LA U. S. A. WRMI 5850 0700-1030 Af Vatican City Vatican R. 15550 0700-1200 Af, M-F South Africa Channel Africa 9625 0700-1900 Oc Vanuatu R. Vanuatu 7260 0700-2000 Oc Vanuatu R. Vanuatu 3945 0730-0800 Oc, Sa-Su Australia R. Australia 15240, 15415, 17840 0730-0800 Oc Australia Reach Beyond Aust 15490 0759-1058 Oc New Zealand RNZI 9700 0800-0900 As United Kingdom BBC 17790th drm 0800-0900 As China China R. Int'l 11620, 15350, 15465, 17540 0800-0900 Eu, Sa Italy IRRS 9510ro 0800-0900 As South Korea KBS World R. 9570 0800-0900 Af, Su South Africa S.Afr. Radio Leag.7205, 17660 0800-0900 As, Su-F Palau T8WH 9930 0800-0900 Af Sudan V. of Africa 9505 0800-0900 Af Sudan Voice of Africa R.9505 0800-1000 Af Nigeria V. of Nigeria 15120 0800-1500 Eu, Su Netherlands Mighty KBC Radio 6095ge 0805-0858 Oc Australia R. Australia 15240, 15415, 17840 0830-2130 As, Oc Australia ABC N Territory 2325 0830-2130 As, Oc Australia ABC N Territory 2485 0900-0905 Oc, Sa-Su Australia R. Australia 15240, 15415, 17840 0900-0930 As Mongolia V. of Mongolia 12085 0900-1000 Oc China China R. Int'l 13790, 17650 0900-1000 Eu China China R. Int'l 17490, 17570, 17650 0900-1000 As China China R. Int'l 11620, 11635, 13570, 13590, 13720, 15350, 17750 0900-1000 As Palau T8WH 9930 0900-1000 Oc, Su-F U. S. A. WHRI 11565 0900-1000 Eu U. S. A. WWCR1 15795 0900-1300 As U. S. A. WEWN 11520 0930-1000 Oc Australia R. Australia 9580, 12065, 12085 0930-1200 Eu, Su Italy IRRS 9510ro 1000-1020 Oc, M-F Guam KTWR 11840 1000-1030 Oc, Sa-Su Australia R. Australia 9580, 12065, 12085 1000-1030 Oc Japan R. Japan 9625 1000-1030 As Vietnam V. of Vietnam 9840, 12020 1000-1030 NA U. S. A. WRMI 5850 1000-1057 LA North Korea V. of Korea 11710, 15180 1000-1057 As North Korea V. of Korea 11735, 13650 1000-1100 As India All India R. 13605, 15030, 15410 1000-1100 Oc India All India R. 13695, 17510, 17895 drm 1000-1100 As United Kingdom BBC 21660th 1000-1100 As China China R. Int'l 11610, 13590, 13720, 15350, 17750 1000-1100 Eu China China R. Int'l 17490 1000-1100 Oc China China R. Int'l 13790, 15210 1000-1100 As Alaska KNLS 9655 1000-1100 LA,Su U. S. A. Overcomer Ministry9610wh 1000-1100 Oc Australia R. Australia 9580, 12065, 12085 1000-1100 Oc Indonesia V. of Indonesia 9526 1000-1100 Eu, Su-F U. S. A. WWCR1 15795 1000-1200 As United Kingdom BBC 6195si, 9740si, 15510si 1000-1200 As,M,W,Th United Kingdom BBC 17830th 1000-1200 As,Su,Tu,F United Kingdom BBC 17790th 1000-1200 As,Sa United Kingdom BBC 17790th 1000-1200 As, Sa-Su Palau T8WH 9930 1000-1225 Af Saudi Arabia BSKSA 15250 1000-1400 LA U. S. A. WRMI 9955 1000-1500 Af Nigeria V. of Nigeria 9690 1000-2200 Am U. S. A. Overcomer Ministry11825wr 1000-2200 Am Anguilla Wld Univ Network 11775 1020-1120 As Iran VOIRI 17640, 17820 1030-1100 As U. S. A. AWR 17730sl 1030-1110 As, M-F Guam KTWR 11965 1059-1258 Oc New Zealand RNZI 9700 1100-1104 Eu Pakistan R. Pakistan 15730, 17730 1100-1115 Eu U. S. A. WWCR1 15795 1100-1130 Eu, Sa South Korea KBS World R. 9760uk drm 1100-1130 Eu, F Japan R. Japan 9760uk drm 1100-1200 As China China R. Int'l 5955, 11650, 11660, 11795, 13590, 13720, 15660 1100-1200 NA, M-F U. S. A. Overcomer Ministry5890wc 1100-1200 LA U. S. A. Overcomer Ministry15320wh 1100-1200 Oc Australia R. Australia 9580, 12065, 12085 1100-1200 Eu Romania R. Romania Int'l 15130, 17680 1100-1200 Af Romania R. Romania Int'l 15150, 17670 1100-1200 As Taiwan R. Taiwan Int'l 7445 1100-1300 Eu China China R. Int'l 13665al, 17490 1115-1130 As,Su-Tu,ThAustralia Reach Beyond Aust 15200 1115-1145 Eu, Sa-Su U. S. A. WWCR1 15795 1130-1145 As, F U. S. A. Eternal Good News 15525ae 1130-1145 LA, Su Cyprus FG Radio 9955wr 1130-1145 As,Sa Australia Reach Beyond Aust 15200 1130-1200 As, Sa U. S. A. Bible Voice 21480ma 1130-1200 LA, M-F Slovakia R. Slovakia 9955wr 1130-1200 As Vietnam V. of Vietnam 9840, 12020 1130-1200 ME, F Vatican City Vatican R. 17590, 21560 1145-1200 Eu U. S. A. WWCR1 15795 1200-1230 As Japan R. Japan 11740si 1200-1230 LA, M-Sa Czech Republic R. Prague 9955wr 1200-1230 As, Sa-Su Palau T8WH 9930 1200-1300 As United Kingdom BBC 6195si, 9740si, 11750th 1200-1300 As, Sa U. S. A. Bible Voice 21480ma 1200-1300 Eu China China R. Int'l 17630 1200-1300 As China China R. Int'l 5955, 9460, 9600, 9645, 9730, 11690, 11980 1200-1300 Oc China China R. Int'l 9760, 11760 1200-1300 As Alaska KNLS 11870 1200-1300 LA,M-Sa U. S. A. Overcomer Ministry15320wh 1200-1300 Oc Australia R. Australia 9580, 12065, 12085 1200-1300 Am, Su U. S. A. WHRI 7315, 9840 1200-1300 NA, Su U. S. A. WHRI 11880 1200-1400 As,M,W,Sa United Kingdom BBC 5810th 1200-1400 As,Tu,Th,F United Kingdom BBC 5830th 1200-1400 As,Su United Kingdom BBC 5875th 1200-1400 NA, M-F U. S. A. Overcomer Ministry9980wc 1200-1500 NA, Sa-Su U. S. A. Wld Univ Network 13845wc 1200-1500 Af U. S. A. WWCR2 7490 1200-1500 NA, M-F U. S. A. WWCR3 13845 1200-1550 Eu U. S. A. Overcomer Ministry21800bu 1200-2100 Eu U. S. A. WWCR1 15825 1215-1230 As, Su U. S. A. Bible Voice 21480ma 1215-1330 ME Egypt R. Cairo 17870, 17480 alt 1230-1245 As, Su U. S. A. Eternal Good News 9930pa 1230-1245 As, Sa Palau T8WH 9930 1230-1300 As Bangladesh Bangladesh Betar 15105 1230-1300 As, Oc Thailand R. Thailand 9390 1230-1300 As Vietnam V. of Vietnam 9840, 12020 1230-1325 Eu Turkey V. of Turkey 15450 1230-1330 As South Korea KBS World R. 6095 1230-1500 LA, Su U. S. A. WINB 9265 1245-1300 As, Sa-Su Palau T8WH 9930 1300-1315 LA, W Cyprus FG Radio 9955wr 1300-1357 NA North Korea V. of Korea 9435, 11710 1300-1357 Eu North Korea V. of Korea 13760, 15245 1300-1400 As United Kingdom BBC 6195si, 9740si, 15310th, 17790om 1300-1400 NA China China R. Int'l 9570cu 1300-1400 Eu China China R. Int'l 13670, 17630 1300-1400 As China China R. Int'l 5955, 9730, 9765, 9870, 11660, 11910, 11980, 13755 1300-1400 Oc China China R. Int'l 11760, 11900 1300-1400 As South Korea KBS World R. 9570 1300-1400 NA South Korea KBS World R. 15575 1300-1400 Af,Sa-Su U. S. A. Overcomer Ministry21610wh 1300-1400 Oc Australia R. Australia 9580, 12065, 12085 1300-1400 As, Sa-Su Palau T8WH 9930 1300-1400 As Indonesia V. of Indonesia 9526 1300-1400 As,ME,Eu Tajikistan V. of Tajik 7245 1300-1430 As, M-Sa Palau T8WH 9930 1300-1550 Oc New Zealand RNZI 6170 1300-1600 As U. S. A. WEWN 15610 1300-1600 NA, Su U. S. A. WHRI 9840 1330-1345 As, Sa United Kingdom FEBA 9720sl 1330-1400 As Laos Lao National Radio7145 1330-1400 As, Th Japan Shiokaze 5985 1330-1400 As Vietnam V. of Vietnam 9840, 12020 1330-1415 As, M United Kingdom FEBA 9720sl 1330-1445 As Australia Reach Beyond Aust 12075 1330-1500 As India All India R. 9690, 11620, 13710 1345-1400 LA, Tu Cyprus FG Radio 9955wr 1400-1430 As, Su U. S. A. Pan American B/C 15205fr 1400-1430 As Japan R. Japan 11705pa, 15735uz 1400-1430 As, Oc Thailand R. Thailand 9390 1400-1430 As, Th Japan Shiokaze 5985 1400-1500 As United Kingdom BBC 5845th drm, 11890si, 15310om 1400-1500 Eu China China R. Int'l 13710, 17630 1400-1500 Af China China R. Int'l 13685ml, 17630ml 1400-1500 As China China R. Int'l 5955, 9765, 9870, 11675 1400-1500 NA China China R. Int'l 15700cu 1400-1500 ME China China R. Int'l 11665 1400-1500 As South Korea KBS World R. 9640 1400-1500 Af, Sa U. S. A. Overcomer Ministry21600wh 1400-1500 Oc Australia R. Australia 9580, 12065, 12085 1400-1500 Eu Oman R. Sultanate Oman 15140 1400-1500 Af U. S. A. V. of America 4930bt, 6080sa, 15580sa 1400-1500 ME,Af, Su U. S. A. WHRI 21600 1400-1600 Eu, Sa-Su U. S. A. Overcomer Ministry13810fr 1400-1600 Eu, M-F U. S. A. Overcomer Ministry13810ge 1400-2100 Af Equ Guinea R. Africa 17790wr 1400-2200 NA U. S. A. Overcomer Ministry9980wc 1400-2200 NA U. S. A. WJHR 15550 USB 1400-2400 NA U. S. A. Overcomer Ministry9370wb 1400-2400 NA,Eu U. S. A. WTWW 9475 1415-1430 As, M-F U. S. A. Pan American B/C 15205ge 1430-1445 As, Su U. S. A. Pan American B/C 15205ge 1430-1500 As, Sa-Su Palau T8WH 11955 1430-1500 As Myanmar Thazin R. 6165 1445-1600 As Australia Reach Beyond Aust 15340 1500-1518 As, M-Sa Guam KTWR 15110 1500-1530 As, Su Guam KTWR 15110 1500-1530 As, Af Vietnam V. of Vietnam 7285, 9840, 12020 1500-1557 NA North Korea V. of Korea 9435, 11710 1500-1557 Eu North Korea V. of Korea 13760, 15245 1500-1600 Af United Kingdom BBC 12095ma, 15420za 1500-1600 As United Kingdom BBC 5845th drm, 7465th, 11890si 1500-1600 ME United Kingdom BBC 9410om, 11675om 1500-1600 Af, M-F South Africa Channel Africa 9625 1500-1600 Eu China China R. Int'l 13640, 15245 1500-1600 As China China R. Int'l 5955, 7325, 7395, 9785, 9870, 9880 1500-1600 Af, ME China China R. Int'l 11610 1500-1600 NA China China R. Int'l 15700cu 1500-1600 Af China China R. Int'l 13685ml, 17630ml 1500-1600 ME China China R. Int'l 9720 1500-1600 As Alaska KNLS 9920 1500-1600 As, Su U. S. A. Pan American B/C 15260fr 1500-1600 Oc Australia R. Australia 9580, 12065, 12085 1500-1600 As, Sa Palau T8WH 11870 1500-1600 Af U. S. A. V. of America 4930bt, 6080sa, 15580bt, 17895bt 1500-1600 Af Nigeria V. of Nigeria 15120 1500-1600 ME, Sa-Su U. S. A. WHRI 21600 1500-1600 NA, Su U. S. A. WHRI 17765 1500-1655 Af U. S. A. Overcomer Ministry11600bu 1500-1700 NA, Su-F U. S. A. Wld Univ Network 13845wc 1500-1700 NA, Sa U. S. A. WWCR3 13845 1500-1800 LA, Sa-Su U. S. A. WINB 9265 1500-2000 Af U. S. A. WWCR2 12160 1515-1530 As, F-Sa Canada Bible Voice 15640ge 1520-1620 As Iran VOIRI 11640, 13780 1530-1545 As India All India R. 9910 1530-1545 As, Sa Canada Bible Voice 15640ge 1530-1600 As, Sa-W U. S. A. AWR 15670ge 1530-1600 As Mongolia V. of Mongolia 12015 1530-1600 As Vatican City Vatican R. 11695ph, 15470ph, 17485 1551-1745 Oc New Zealand RNZI 5975, 7330 drm 1600-1630 As U. S. A. AWR 11995sl 1600-1630 As Guam KSDA 15530 1600-1630 As, Th Japan Shiokaze 5985 1600-1630 Eu, Af, As Vietnam V. of Vietnam 7220, 7280, 9550, 9730 1600-1657 ME North Korea V. of Korea 9890, 11645 1600-1700 Af United Kingdom BBC 3255za, 6190za, 12095ma, 15420za, 17640as, 17830as 1600-1700 As United Kingdom BBC 5845th drm, 7465th, 11890si 1600-1700 ME United Kingdom BBC 7375om, 9410om 1600-1700 As China China R. Int'l 6060, 6175, 7235, 9880 1600-1700 Eu China China R. Int'l 11940, 11965, 13760 1600-1700 Af China China R. Int'l 9570, 11900 1600-1700 Af, ME China China R. Int'l 15250 1600-1700 Eu South Korea KBS World R. 9515 1600-1700 As South Korea KBS World R. 9640 1600-1700 As U. S. A. Overcomer Ministry9930pa 1600-1700 As China PBS Zizang Lhaza 4905, 4920, 6025, 6110, 6130, 6200, 7255, 7385 1600-1700 Oc Australia R. Australia 9580, 12065, 12085 1600-1700 As Taiwan R. Taiwan Int'l 6180 1600-1700 Af U. S. A. V. of America 4930bt, 6080sa, 15580bt 1600-1730 Af U. S. A. WHRI 21600 1600-1800 NA U. S. A. Overcomer Ministry9840wh 1600-1800 Af Egypt R. Cairo 15345 1600-1855 Eu, Tu-Th U. S. A. Overcomer Ministry21800bu 1600-1855 Eu, Sa-Su U. S. A. Overcomer Ministry21800bu 1600-1900 ME U. S. A. WEWN 15610 1615-1629 ME Vatican City Vatican R. 15595 1630-1700 As, M,W,F Guam AWR 15360 1630-1700 As, Th Japan Shiokaze 5985 1630-1700 Af, M-F U. S. A. V. of America 11845za, 13865, 15180va 1630-1725 As Turkey V. of Turkey 15520 1630-1730 Af, M South Africa S.Afr. Radio Leag.4895 1700-1715 ME, F Canada Bible Voice 15215au 1700-1715 ME, Sa U. S. A. Eternal Good News 15215au 1700-1715 Af United Kingdom FEBA 6180ae 1700-1730 ME, Su,Th Canada Bible Voice 15215au 1700-1730 Af U. S. A. V. of America 6080za, 13590va, 15580bt, 17895sl 1700-1730 Eu Vietnam V. of Vietnam 9625au 1700-1755 Af, M-F South Africa Channel Africa 15235 1700-1800 Af United Kingdom BBC 3255za, 6190za, 7445ma, 9410ae, 15400as, 17780as, 17830as 1700-1800 As United Kingdom BBC 5845th drm 1700-1800 ME United Kingdom BBC 6195om, 7375om 1700-1800 As China China R. Int'l 6090, 6140, 6175, 7235, 7410, 7420, 9880 1700-1800 ME China China R. Int'l 6165 1700-1800 Af China China R. Int'l 9570, 11900 1700-1800 Eu China China R. Int'l 12015, 13760 1700-1800 Oc Australia R. Australia 9580, 12065, 12085 1700-1800 Eu Romania R. Romania Int'l 5940, 11810 drm 1700-1900 ME,Sa Canada Bible Voice 15215au 1700-1900 NA U. S. A. WTWW 12105 1700-2400 NA U. S. A. Wld Univ Network 13845wc 1720-1740 Af, F-Su U. S. A. V. of America 4930bt, 6065bt, 15460sa 1730-1745 Af, Sa U. S. A. Eternal Good News 21600wh 1730-1745 Af, Su-F U. S. A. WHRI 21600 1730-1757 Af Vatican City Vatican R. 11625, 13765, 15570 1730-1800 Eu, Su Canada Bible Voice 6130ge 1730-1800 Af U. S. A. V. of America 6080sa, 13590va, 15580bt, 17895gr 1730-1800 Af, M-Th U. S. A. V. of America 4930bt, 6065bt, 15460sa 1730-1830 Af Sudan Voice of Africa R.9505 1730-1930 ME Philippines R. Pilipinas 9905, 12120, 15190 1745-1800 Af U. S. A. WHRI 21600 1745-1900 Eu Bangladesh Bangladesh Betar 13580 1745-1945 Af India All India R. 9445, 11580, 11935, 13695, 17670 1745-1945 Eu India All India R. 7550, 9950 drm, 11670 1746-1835 Oc New Zealand RNZI 9700, 7330 drm 1800-1810 Af Tanzania Zanzibar B/C 11735 1800-1815 Af Cyprus FG Radio 13600bu 1800-1830 Af Japan R. Japan 9755za 1800-1830 Af Swaziland TWR Africa 9500 1800-1830 Af U. S. A. V. of America 4930bt Sa-Su, 6080sa, 15580bt 1800-1830 LA,Tu,W,F U. S. A. WINB 9265 1800-1857 Eu North Korea V. of Korea 13760, 15245 1800-1900 ME United Kingdom BBC 6195om, 7375om 1800-1900 ME, Su Canada Bible Voice 15215au 1800-1900 Eu China China R. Int'l 9600, 13760 1800-1900 Eu, F-Su Italy IRRS 7290ro 1800-1900 Eu South Korea KBS World R. 7275 1800-1900 Af, M-F U. S. A. Overcomer Ministry21600wh 1800-1900 Oc Australia R. Australia 9580, 12065, 12085 1800-1900 ME Yemen R. Sanna 6135 1800-1900 Eu,M-F Argentina RAE 9690, 15345 1800-1900 Af, Sa-Su U. S. A. WHRI 21600 1800-1900 NA U. S. A. WHRI 9840 1800-1930 Af Nigeria V. of Nigeria 9690 1800-2000 Af United Kingdom BBC 3255za, 6190za, 7445ma, 9410ae, 11810as, 13660, 15400as 1815-1830 ME, Su Canada Bible Voice 9435ge 1815-1830 As, Su U. S. A. Eternal Good News 11855ge 1815-1900 Af U. S. A. Overcomer Ministry13600bu 1830-1845 Eu, Sa U. S. A. Eternal Good News 6130ge 1830-1900 Af U. S. A. AWR 11840za 1830-1900 Af U. S. A. V. of America 4930bt, 6080bt, 15580bt 1830-1900 LA U. S. A. WINB 9265 1830-1915 ME, Su Canada Bible Voice 9635ge 1830-1925 Eu Turkey V. of Turkey 9785 1830-2000 Af Nigeria V. of Nigeria 15120 drm 1836-1850 Oc New Zealand RNZI 9700, 9760 drm 1845-1900 Eu, Sa Cyprus FG Radio 5900bu 1851-1950 Oc New Zealand RNZI 11725, 11690 drm 1900-1930 Eu, As Vietnam V. of Vietnam 7280, 9730 1900-1957 ME North Korea V. of Korea 9875, 11635 1900-1957 Af North Korea V. of Korea 7210, 11910 1900-2000 Oc United Kingdom BBC 9855si 1900-2000 Af, ME China China R. Int'l 7295, 9440 1900-2000 Af, M-F U. S. A. Overcomer Ministry17610wh 1900-2000 NA, Su U. S. A. Overcomer Ministry9840wh 1900-2000 Oc Australia R. Australia 9580, 12065, 12085 1900-2000 LA Cuba R. Havana Cuba 11760 1900-2000 Eu Thailand R. Thailand 9390 1900-2000 Af U. S. A. V. of America 4930bt, 6080bt, 15580bt 1900-2000 Eu Indonesia V. of Indonesia 9526 1900-2000 Am, Tu U. S. A. WBCQ 7490 1900-2000 NA, M-F U. S. A. WHRI 9840 1900-2000 NA, Su U. S. A. WHRI 17765 1900-2000 LA, Sa U. S. A. WHRI 9495 1900-2030 Af Egypt R. Cairo 15290 1900-2100 LA, M-F U. S. A. Overcomer Ministry9265wi 1900-2100 LA,Sa-Su U. S. A. WINB 9265 1900-2400 Af U. S. A. WEWN 15610 1920-2020 Af Iran VOIRI 9400, 11885 1920-2020 Eu Iran VOIRI 9715, 11985 1930-2000 ME, Af, Su U. S. A. Pan American B/C 9515ge 1930-2000 Af, M-F Ireland R. Telefís Éireann5820za 1951-2050 Oc New Zealand RNZI 11725, 15720 drm 2000-2020 Eu,Tu,W,F Belarus R. Belarus 11730, 11930 2000-2027 Af Vatican City Vatican R. 13765, 15570 2000-2030 Eu, M-Sa Albania R. Tirana 7465 2000-2030 Af U. S. A. V. of America 4930bt, 6080bt, 15580bt 2000-2058 Oc Australia R. Australia 9580, 12065, 12085 2000-2100 Af United Kingdom BBC 9915, 11810as, 12095as 2000-2100 Af China China R. Int'l 5985, 11640ml, 13630ml 2000-2100 Eu China China R. Int'l 5960al, 7285al, 7415, 9600 2000-2100 Af, ME China China R. Int'l 7295, 9440 2000-2100 ME China China R. Int'l 9440 2000-2100 LA, M-Sa U. S. A. Overcomer Ministry11670wh 2000-2100 Am, M-F U. S. A. WBCQ 7490 2000-2100 NA, Sa-Su U. S. A. WHRI 17765 2000-2100 Eu, Su U. S. A. WHRI 15530 2000-2400 Oc Vanuatu R. Vanuatu 7260 2000-2400 Af U. S. A. WWCR2 9350 2020-2200 Eu Belarus R. Belarus 11730, 11930 2030-2045 Eu Thailand R. Thailand 9390 2030-2100 Eu Romania R. Romania Int'l 6170, 9800 drm 2030-2100 NA Romania R. Romania Int'l 13650, 15170 2030-2100 Af U. S. A. V. of America 4930bt, 4940sa Sa-Su, 6080bt, 15580bt 2030-2100 ME Vietnam V. of Vietnam 7220 2030-2100 Eu Vietnam V. of Vietnam 7280, 9730 2030-2100 Af Vietnam V. of Vietnam 9550 2030-2125 As, Oc Turkey V. of Turkey 7205 2045-2230 Eu India All India R. 7550, 9445, 9950 drm, 11670 2045-2230 Oc India All India R. 9910, 11620 drm, 11740 2051-2150 Oc New Zealand RNZI 11725 2051-2150 Oc, Su-F New Zealand RNZI 15720 drm 2100-2115 Eu, Su U. S. A. Eternal Good News 15530wh 2100-2115 Eu, W Cyprus FG Radio 15770wr 2100-2115 NA, W Cyprus FG Radio 7570wr 2100-2130 Af U. S. A. AWR 11955au 2100-2130 Af China China R. Int'l 11640ml, 13630ml 2100-2157 Eu North Korea V. of Korea 13760, 15245 2100-2200 Af, M-F United Kingdom BBC 9915as, 11810as, 12095as 2100-2200 Af China China R. Int'l 7205, 7325 2100-2200 Eu China China R. Int'l 5960al, 7285al, 7415, 9600 2100-2200 Oc Australia R. Australia 15240, 15415, 17840 2100-2200 LA, M-Tu France R. France Int'l 15770wr 2100-2200 LA, Sa France R. France Int'l 15770wr 2100-2200 Af U. S. A. V. of America 6080bt, 15580bt 2100-2200 Am, Su U. S. A. WBCQ 7490 2100-2200 Eu, M-F U. S. A. WHRI 15530 2100-2200 LA, Sa U. S. A. WHRI 11670 2100-2200 LA, Sa-Su U. S. A. WRMI 9955 2100-2200 Eu U. S. A. WRMI 15770 2100-2200 Eu, Sa-Su U. S. A. WWCR1 15825 2100-2300 Af Equ Guinea R. Africa 15190wr 2100-2330 LA U. S. A. WINB 9265 2115-2200 LA, W France R. France Int'l 15770wr 2115-2200 Eu, Su U. S. A. WHRI 15530 2115-2245 Eu Egypt R. Cairo 9800 2130-2200 LA, M-F France R. France Int'l 15770wr 2145-2200 Eu, W Cyprus FG Radio 15770wr 2151-2355 Oc New Zealand RNZI 15720 2200-2230 As,Su,Tu,ThGuam KSDA 15435 2200-2255 NA, Eu Turkey V. of Turkey 9830 2200-2300 As United Kingdom BBC 3915si, 5875th, 5890th, 5905th, 6195si, 7485th, 9740si, 9890om 2200-2300 As China China R. Int'l 9590 2200-2300 Eu South Korea KBS World R. 11810 2200-2300 LA, M-F U. S. A. Overcomer Ministry9955wr 2200-2300 NA, M-F U. S. A. Overcomer Ministry9980wc 2200-2300 LA, Sa-Su U. S. A. Overcomer Ministry11670wh 2200-2300 Eu, M-F U. S. A. Overcomer Ministry11775wh 2200-2300 Am, M-F U. S. A. Overcomer Ministry7490wq 2200-2300 NA,Eu, Tu Taiwan PCJ Radio Int'l 7570wr, 15770wr 2200-2300 Oc Australia R. Australia 15240, 15415, 17840 2200-2300 Eu Romania R. Romania Int'l 5930, 7430 2200-2300 As Romania R. Romania Int'l 9790, 11700 2200-2300 Am, Sa-Su U. S. A. WBCQ 7490 2200-2300 NA, Sa-Su U. S. A. WHRI 11775 2200-2300 NA, F U. S. A. WHRI 7385 2200-2300 LA, W-Su U. S. A. WRMI 9955 2200-2400 NA U. S. A. Overcomer Ministry7570wr 2200-2400 Eu U. S. A. Overcomer Ministry15770wr 2200-2400 Am Anguilla Wld Univ Network 6090 2200-2400 NA U. S. A. WWCR1 6115 2200-2400 NA U. S. A. WWRB 3215 2245-2400 As India All India R. 9690, 9705, 11645 drm, 11710, 13605 drm 2300-2315 Eu, Tu Cyprus FG Radio 11580wr 2300-2315 Eu, Th Cyprus FG Radio 11580wr 2300-2315 As, Su Australia Reach Beyond Aust 11765 2300-2400 As United Kingdom BBC 5875th, 6195si, 9740si, 9890th, 11850si, 12010th 2300-2400 LA China China R. Int'l 5990cu 2300-2400 As China China R. Int'l 5915, 7410, 11690, 11790, 11955 2300-2400 Eu China China R. Int'l 7350 2300-2400 LA U. S. A. Overcomer Ministry5050wb 2300-2400 Af U. S. A. Overcomer Ministry15190wr 2300-2400 Eu, M-F U. S. A. Overcomer Ministry11775wh 2300-2400 LA, Sa U. S. A. Overcomer Ministry7315wh 2300-2400 LA, F Taiwan PCJ Radio Int'l 9955wr 2300-2400 Oc Australia R. Australia 15240, 15415, 17840 2300-2400 NA Egypt R. Cairo 9965 2300-2400 LA Cuba R. Havana Cuba 5040 2300-2400 Af Cuba R. Havana Cuba 11880 2300-2400 Am U. S. A. WBCQ 7490 2300-2400 LA, Su-F U. S. A. WHRI 7315 2300-2400 NA, Sa U. S. A. WHRI 11775 2300-2400 Eu U. S. A. WRMI 11580 2300-2400 LA U. S. A. WRMI 9955 2300-2400 NA, M-F U. S. A. WWCR4 9980 2330-2400 As, Sa-Su Guam KSDA 15320 2330-2400 Eu Ukraine R. Ukraine Int'l 11580wr 2330-2400 As Vietnam V. of Vietnam 9840, 12020 2330-2400 LA, Tu-Su U. S. A. WINB 9265 2345-2400 LA,Su U. S. A. Eternal Good News 7315wh This shortwave schedule list is intended for personal use only. Any other use without giving credit to or getting permission from Daniel Sampson, This email address is being protected from spambots. You need JavaScript enabled to view it., and giving credit to the Prime Time Shortwave website is strictly prohibited.
Shortwave info
Thank you for this updated information http://www.primetimeshortwave.com/
Phonetic Alphabet
| Phonetic Alphabet | |||
| A | Alpha | N | November |
| B | Bravo | O | Oscar |
| C | Charlie | P | Papa |
| D | Delta | Q | Quebec |
| E | Echo | R | Romeo |
| F | Foxtrot | S | Sierra |
| G | Golf | T | Tango |
| H | Hotel | U | Uniform |
| I | India | V | Victor |
| J | Juliet | W | Whiskey |
| K | Kilo | X | X-ray |
| L | Lima | Y | Yankee |
| M | Mike | Z | Zulu |
400MHZ Chart
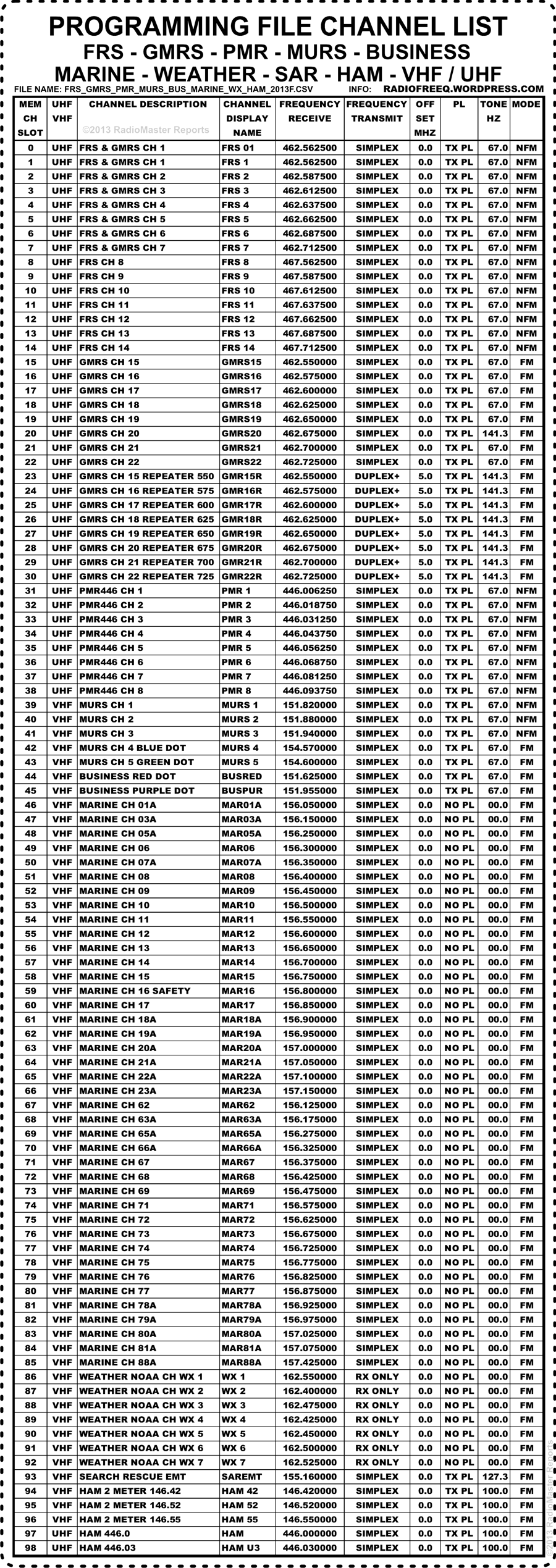
Thanks to https://radiofreeq.wordpress.com
NOTE: SAREMT is for Emergency use only! Do Not Transmit on this frequency unless you have an Emergency.
SDR Using a RaspberryPi and RPITX
- Published: 21 April 2020 21 April 2020
SDR with a transmitter see reference here -> https://github.com/F5OEO/rpitx
rpitx is a general radio frequency transmitter for Raspberry Pi which doesn't require any other hardware unless filter to avoid intererence. It can handle frequencies from 5 KHz up to 1500 MHz.
Rpitx is a software made for educational on RF system. It has not been tested for compliance with regulations governing transmission of radio signals.
Apache htaccess
- Published: 27 November 2012 27 November 2012
Apache htaccess New User and file
Make a new user name on .htacApache, htaccesscess (see below)
At the command Line Type:
htpasswd .htpasswd username
to add a new usere to the .htpasswd NOTE: Only us the -c (htpasswd -c .htpasswd username)to create the file DON"T use -c if File exist it will erase all the other users. The program will initially prompt you for a password and then ask you to verify it.
The .htaccess file below must contain
AuthUserFile /kunden/homepages/http/website/foldertoprotect/.htpasswd AuthGroupFile /dev/null AuthName "Download Area" AuthType Basic <limit get="" post=""> require valid-user </limit>
Note the AuthUserFile must be from root and end with the password file name. AuthName is the name in the password popup window change as needed. IN ADDITION verify you are using the correct path - telnet in and type pwd, use the path that echo's back
Restart Apache service use the command below
sudo /etc/init.d/apache2 restartDiversify Your Financial Risk When Investing In Cryptocurrencies
- Published: 10 February 2020 10 February 2020
Diversify your financial risk when investing in Cryptocurrencies.
You no longer need to be a computer geek to invest in one of the fastest growing financial markets. Cryptocurrencies also known as Bitcoin, Ethereum, Litecoin, Tezos, and hundreds more, are really taking off. So your fear of investing, may have swayed you away from this profitable investment, but companies like CoinBase (USA Based Company) have made it easy to be an investor.
Coinbase will allow you, the investor, to connect your bank account to their fast and secure trading platforms. This allows you to easily deposit cash in and start investing.
- Coinbase is the world’s largest Bitcoin broker, and also offers an exchange, wallet, and developer API.
- Coinbase Pro (Formerly GDAX) is their world-class interface that provides real time order books, charting tools, trade history, and a simple order process so you can start trading immediately.
- They have a top rated help desk for you to get started. I have personally email them and got a response almost immediately. In addition all of my request were resolved.
- iPhone and Android trading ready.
So the fear of investing has been resolved by Coinbase.com, so take some time and do your homework, and check out Coinbase.com and Pro.Coinbase.com.
Python - Add a message box
- Published: 23 February 2019 23 February 2019
Add a message box to your Python code. Use the ctype library with is already in the core Python library..
[code]## add a message box for Windows only parameters below for different box types
# ## Styles:
## 0 : OK
## 1 : OK | Cancel
## 2 : Abort | Retry | Ignore
## 3 : Yes | No | Cancel
## 4 : Yes | No
## 5 : Retry | No
## 6 : Cancel | Try Again | Continue
## To also change icon, add these values to previous number
# 16 Stop-sign icon
# 32 Question-mark icon
# 48 Exclamation-point icon
# 64 Information-sign icon consisting of an 'i' in a circle
import ctypes
#print(dir(ctypes)) # displays all the functions in the library
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 0', 0)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 1', 1)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 2', 2)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 3', 3)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 4', 4)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 5', 5)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 6', 6)
ctypes.windll.user32.MessageBoxW(0, 'Error in your code today', 'Error message title 16', 16)[/code]
Windows Check Sum Hash Algorithm from CMD
- Published: 19 January 2019 19 January 2019
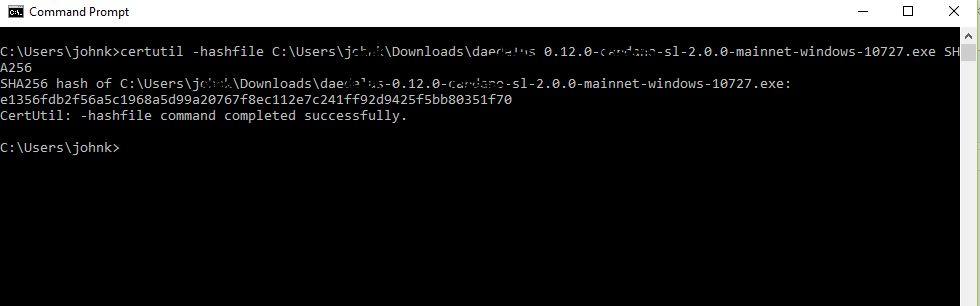
Yes Window 10 (and Windows 7) had a built in Hash Tag Checksum tool. So when you download a file, you can verify that this file has not been tampered with. This tool is from Windows Command Line - CMD. It will generate a key for all these HASHES - MD2 MD4 MD5 SHA1 SHA256 SHA384 SHA512
Open a command line windows - CMD, Make sure you know that path where the download file is located. Verify the Hash Tag Algorithm from the website. Type in the following:
certUtil -hashfile C:\owner\download\MyDataFile.img SHA256
For example you can see I downloaded a file from this site (on the left) and it gives the SHA256 Checksum code you should expected when running the certutil.
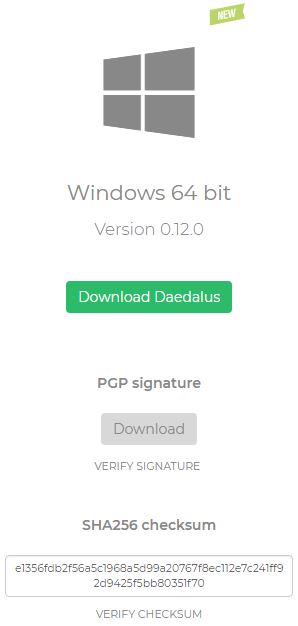
Protect Your Personal Identity - Wipe That Hard Drive
- Published: 21 August 2016 21 August 2016
To protect your personal identity you need to wipe your HD clean from all your personal data. Try DBAN, which is a free SSD and hard disk utility that will nuke all your data. Check out the YouTube video below how2 wipe all personal data. So, you can eliminate the virus, or wipe the drive reload your operating system so you can resell your system, or just distroy the HD, so that no one can see what has been saved.
Here is the link to an instructional video on DBAN
Here is an alternative to deal with your use unwanted hard drive, simply to destroy it. Find a local shredding company, to see if they shred your drive/electronics. This is eco-friendly and it should make you feel better, not even the government can see your data after this destruction. Watch this video just to see how your drive is destroyed, and how they recycle all of the parts. Also look for free community service events. they usually provided by your city, count. These events usually offer dangerous waste collections, shredded of documents and a computer shredding service.
In Kali LINUX you can use a command below:
shred -vfz -n 10 /dev/sda
MySQL Dump
- Published: 14 April 2016 14 April 2016
A Simple Database Backup
mysqldump -h [hostorIP] -u [username] -p [password] [databasename] > [backupfile.sql]
{easycodeinc /article_code_snippets/MySQL_Dump_Restore.php, 1, php, linenums:1}
- [host or IP] - is your connection to the sql server
- [username] - this is your database username
- [password] - this is the password for your database
- [databasename] - the name of your database
- [backupfile.sql] - the file to which the backup should be written.
The resultant dump file will contain all the SQL statements needed to create the table and populate the table in a new database server. To backup your database 'Customers' with the username 'sadmin' and password 'pass21' to a file custback.sql, you would issue the command:
You can also ask mysqldump to add a drop table command before every create command by using the option --add-drop-table. This option is useful if you would like to create a backup file which can rewrite an existing database without having to delete the older database manually first.
To restore the dump... The "<" before the file name will restore all the table to the Customers database
htaccess Tutorial
- Published: 27 November 2012 27 November 2012
htaccess Tutorial
This tutorial will demonstrate how to use .htaccess files to perform several basic Apache and PHP configurations at the directory level. This tutorial makes the following assumptions:
* You are using Apache as your webserver.
* Your web host has enabled .htaccess override for your account.
* For the PHP configuration, you must be running PHP as an Apache module.
If you're not sure about whether these statements are true, check with your web host's technical support department.
There several types of configuration that can be performed using a .htaccess file. These include authorization, redirects, changing the index file name, displaying custom error pages, and changing PHP configuration settings.
To perform such configuration, simply create a file named .htaccess (the dot in front is required) in the folder where you would like the settings to be applied. Any settings you configure for this directory will also be applied recursively to all of its sub directories. Note that some FTP clients may be configured to hide files that start with a dot. If this is the case, you may need to reconfigure your FTP client to display these files.
Changing the index file name
The index file is the file that gets displayed automatically when a user browses to a directory. Historically, the index file is called index.html or index.htm. On a PHP powered site, you may want your index file to be named index.php. This can be accomplished by putting the following line in your .htaccess file:
DirectoryIndex index.php index.html
The directive above instructs Apache to use index.php as the index file if it exists, otherwise it should look for a file named index.html. If neither file exists in the requested directory, the user will usually get a directory listing.
Using a custom error page
Everyone at one point or another encounters the dreaded "HTTP 404 - File Not Found" error message. Perhaps the user followed a broken link, or mistyped the URL of the page they were looking for. The default error page is usually quite ugly. However, it is possible to use a custom error page for this or any other HTTP error. This can be done by placing the line below in your .htaccess file:
ErrorDocument 404 http://www.mysite.com/404.html
Replace "http://www.mysite.com/404.html" with the URL for the page you want the user to see when they request a missing file.
It is important that your custom "file not found" page returns the HTTP 404 status code, otherwise your site could be penalized by the search engines. You can do this by adding the following PHP code at the top of your 404 page.
header("HTTP/1.0 404 Not Found");
Denying access to a directory
Sometimes, there may be directories on your website that the user shouldn't be able to directly request files from. For example, you may have a directory that stores data files for your scripts, or a set of PHP includes. Placing the lines below in the .htaccess file for that directory will block direct requests for those files:
Order Deny,Allow
Deny from all
The first line ensures that the deny directive is evaluated before any allow directives that may have been defined elsewhere in the directory hierarchy.
Redirecting requests
Over time, files on a website may get moved or renamed. Rather than letting the user to see a 404 error message when requesting the old file, you can redirect them to the new file using the following directive:
Redirect permanent /old.php http://www.mysite.com/new.php
The permanent keyword indicates that an HTTP 301 ("resource has moved permanently") status code should be returned to the web browser. Replace "old.php" with the path to the old file, and "http://www.mysite.com/new.php" with the URL to the new file.
PHP configuration
Lastly, .htaccess files can be used to change PHP settings when running as an Apache module. Such configuration is performed using the php_value and php_flag directives. Use the later when the setting takes a boolean value. For example, to turn off register globals from .htaccess, use the following line:
php_flag register_globals off
The following directive can be used to turn off magic quotes for all PHP scripts in a directory:
php_flag magic_quotes_gpc off
To enable or disable error reporting, use the php_flag directive to set the display_errors flag. Enabling this flag will cause error messages to be displayed in the browser, e.g.:
php_flag display_errors on
To hide error messages from the end user, simply disable the display_errors flag:
php_flag display_errors off
Add a HTML Link with no underline
- Published: 27 November 2011 27 November 2011
use the deceleration of style="text-decoration: none;" after the URL link. See source below